API Manager single sign-on
4 minute read
Single sign-on (SSO) is a session/user authentication process in which a user enters one user name and password to access multiple applications. API Manager supports SAML-based single sign-on (SSO). This enables users to use the same login details for API Manager and other Axway platform products (for example, API Portal or Decision Insight) and eliminates the need to log in multiple times to different web-based UIs.
SSO concepts
The SAML 2.0 standard describes how to exchange authentication and authorization data between entities. This section describes some key concepts.
Service Provider
A Service Provider (SP) protects access to requested resources, such as web sites and applications by applying a security policy. For example, the SP blocks all access to an unauthenticated user and routes the request to the Identity Provider. API Manager acts as an SP.
Identity Provider
An Identity Provider (IdP) is a system that creates, maintains, and manages identity information for users, services, or systems, and provides authentication to other service providers (applications) within a network. An IdP is a trusted entity that users and servers can rely on when they are establishing a dialog that must be authenticated. The IdP sends an attribute assertion containing trusted information about the user to the SP. In an Axway deployment, the IdP is a third-party product.
User agent
A user agent is usually a web browser. The person who uses the browser can be referred to as a user or as a principal.
Security Assertion Markup Language (SAML)
The Security Assertion Markup Language (SAML) is an XML-based solution for exchanging user security information (authentication, authorization) between an IdP and SP. SAML is a product of the OASIS Security Services Technical Committee.
SAML assertion
A SAML assertion is a package of information that contains one or more statements made by a SAML authority. The SAML standard defines three types of assertion statement:
- Authentication: The specified subject was authenticated by a particular means at a particular time. This kind of statement is typically generated by an IdP.
- Attribute: The specified subject is associated with the supplied attributes.
- Authorization: A decision to grant or deny the specified subject access to the specified resource.
SSO message flows
The following diagram shows a simplified message flow for SSO using SAML:
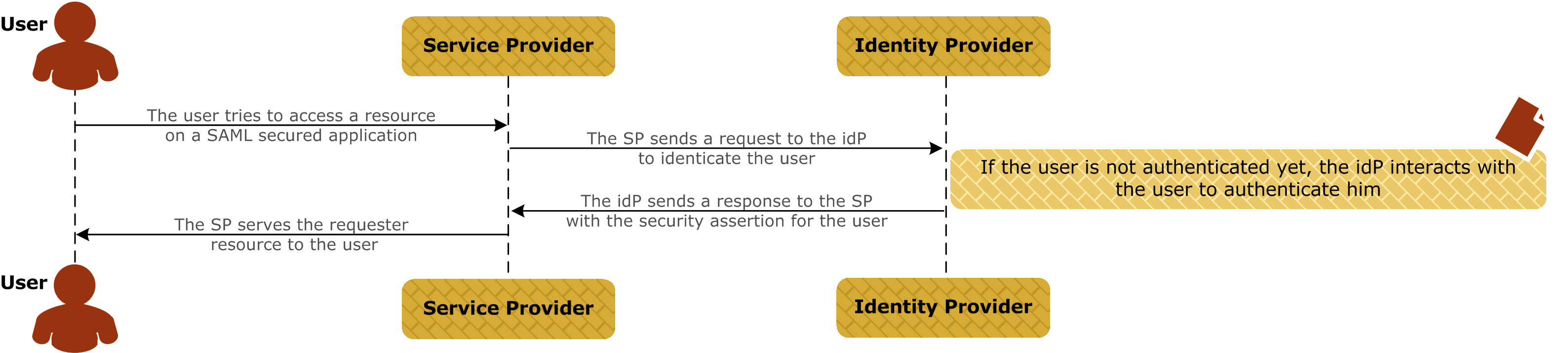
The following sections describe the message flows between API Manager (acting as the SP) and the IdP.
Authentication sequence
When API Manager is configured for SSO, the following events occur during authentication between API Manager and the IdP:
-
The end user tries to access the API Manager UI using a web browser:
- For non-SSO login, access on the default URL (for example,
https://FQDN:8075). - For SSO login, access on the SSO URL (for example,
https://FQDN:8075/api/portal/v1.3/sso/login/). The SSO login URL must be used even if the user has already logged in using SSO (for example, if they have already logged in to API Portal or Decision Insight).
Note
To enable a user to become a member of multiple API Manager organizations, you must use the 1.4 version of the API (https://FQDN:8075/api/portal/v1.4/sso/login/) in the SSO login step. - For non-SSO login, access on the default URL (for example,
-
API Manager builds a SAML Authentication Request message and sends it to the IdP.
-
The IdP receives the request and checks if there is an active session for the user.
-
If no session for this user exists on the IdP, the user is prompted to enter their credentials.
-
The IdP analyzes the credentials and sends a SAML Response message, asserting that the user is authenticated.
-
API Manager maps the user’s IdP role to an API Manager-specific role. For more information, see Mapping syntax.
-
The user is presented with the appropriate view of API Manager, depending on their role.
Logout sequence
The logout sequence is as follows when logout is initiated by API Manager:
- The end user tries to log out of API Manager by clicking the Logout button in the UI.
- API Manager recognizes that the user has an active session, so it generates a SAML Logout Request message and sends it to the IdP.
- The IdP removes the user session and returns a SAML Logout Response to the browser.
- The browser posts the HTML form containing the SAML Logout Response to the API Manager single logout service URI.
- API Manager removes the user session and redirects to the logout redirect URI.